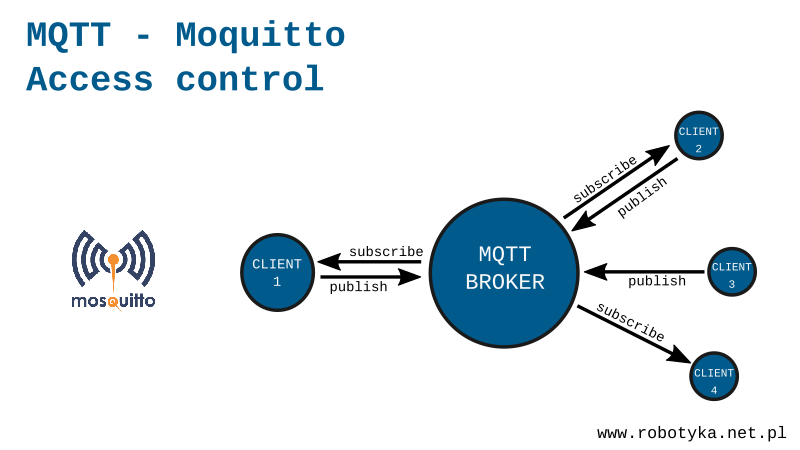
While our broker is located inside the home network does not threaten us that someone is not authorized subscribe, or publish something in our topics, but when the server will be available outside the network we need some secure. It would not be good if someone would not be allowed to control the light in our house, or worse, open the door. The Mosquitto broker has a security system, where without the appropriate login and password to connect with it.
Step 1: Configure the server (mosquitto. conf file)
The first step will be to change the Mosquitto broker configuration. So that it does not allow anonymous users to connect. To do this, we need to modify mosquitto.conf file. One of the ways I’ll give below:
sudo nano/etc/mosquitto/mosquitto.conf
And then add a line at the end of the file:
allow_anonymous false password_file/etc/mosquitto/password_m
Save the file (Ctrl + O) and close the editor (CTRL + X).
The first line prohibits connecting to anonymous users, and the other determines in what file will be the user’s logins and passwords.
Step 2: Create the file with logins and passwords (mosquitto_m file)
In the previous step, we informed broker in what file will be all user logins and passwords. Now we will by created this file. Its structure is very simple. Each line is information about one user in template login:password. To create a file we execute the command:
sudo nano/etc/mosquitto/password_m
and enter the file line with a password and login. In my case it looks like this:
pawel:haslo
“hasło” means password in polish.
Save the file (Ctrl + O) and close the editor (CTRL + X).
Because the Mosquitto broker accepts only coded passwords, we need to use a specially created mosquitto_passwd program. Run it with the command:
sudo mosquitto_passwd-U/etc/mosquitto/password_m
We can preview our coded password with the help of the command:
cat/etc/mosquitto/password_m
It will have the form of:
pawel:$6$QGf6jML4Nzv+rfrN$u3q/Nz7NhsM1uDA6EmsR9ETDVZO3Bh7I8KC4Iu7pQ5fRrEyYFGZrrguNHWxgRW5CcULlOYJX2l9NLzD4cTHArQ==
Password encryption is very useful, now that someone will have access to our computer and see the file password_m it does not know anything beyond the login, because the unencrypted form of the password is only in our biological memory (brain).
Step 3: Reset the Broker
Finally, we need to restart the broker to load the new settings at startup. Use this command:
sudo/etc/init.d/mosquitto restart
Or:
sudo systemctl restart mosquitto
Security test
The anonymous user will no longer be able to connect to such a prepared broker. Now every time we call the mosquitto_sub and mosquitto_pub commands we need to give our login and password. This is used for the arguments -u login, and -P password.
For example, open two terminal windows. In the first we execute the command:
mosquitto_sub -u pawel -P haslo -t myTopic
And in the second:
mosquitto_pub -u pawel-P haslo -t myTopic -m "Message"
The following screenshot shows the action:

Now for checking the firewall set by us we will try to publish the message as an anonymous user without providing any data:
Mosquitto_pub-T MyTopic-M "Message"
As a result, we will get information that our connection is not authorized and has been rejected:

Server logs
It is also worth to look into the logs generated by the server Mosquitto. This can be done by calling:
cat/var/log/mosquitto/mosquitto.log
After it is done, we will see a list of actions which are sections on the server. An interesting line can be:
1532967289: Socket error on client <unknown>,</unknown> disconnecting.
Thanks to this we know that someone anonymously tried to log in but bounced off our defensive wall.
Summary
After doing this, we can safely share our broker for the external network without fear that someone will be able to hack into our home control system. Without the right data, nothing will be done.